Case Study - NOF
NOF
‘Safe’ is becoming a priority in delivery and use of IT systems. Gone are the days when ‘hacking’ was the purview of vandals just looking to cause disruption. Now, it is a criminal enterprise and increasing exponentially. Not only will these criminals encrypt your data and demand a substantial ransom to let you have it back, with no guarantee that you actually will, but they will threaten to publish it online, so further damaging your company’s reputation.
The significant downtime involved in a cyber-attack can put your whole business in jeopardy and there is the further possibility of substantial fines from the Information Commissioner’s Office if you can’t show that you have taken reasonable precautions to protect the data you hold.
We have developed a high level of knowledge and experience in this area and will help you implement the right solutions, procedures and policies to enhance your businesses security.
And this isn’t just about your business. If you are engaged in business-to-business opportunities, those third parties are requiring much more evidence that you have the procedures and systems in place to protect not only your data but their data as well.
We can evaluate your systems, practices and procedures to ensure your environment is protecting your data. We can help you implement cost effective solutions and provide your staff (often the weakest part of a company’s security) with online cybersecurity training so they understand what good practice is and why it is needed.
Cyber Essentials

Having secured certification ourselves and using the Cyber Essentials criteria as a baseline for all our clients, we can guide you through obtaining Cyber Essentials certification for your company. As well as a benchmark for the company, it is becoming a more frequent requirement for business-to-business opportunities.
End User Education
Your team are often the weakest part of any IT security but have the potential to be your best defence against cybercrime; education is key to protecting your organisation’s systems. We can provide online cybersecurity training that will teach your staff the fundamentals of good security practices.
Data Backup
Not only will malicious actors try and remove access to your data but they will also try and destroy your backups, preventing you from recovering from their attacks. We utilise proven technology to keep your backups safe, so if the worst happens, you can still get back on your feet.
End User Training Implementation
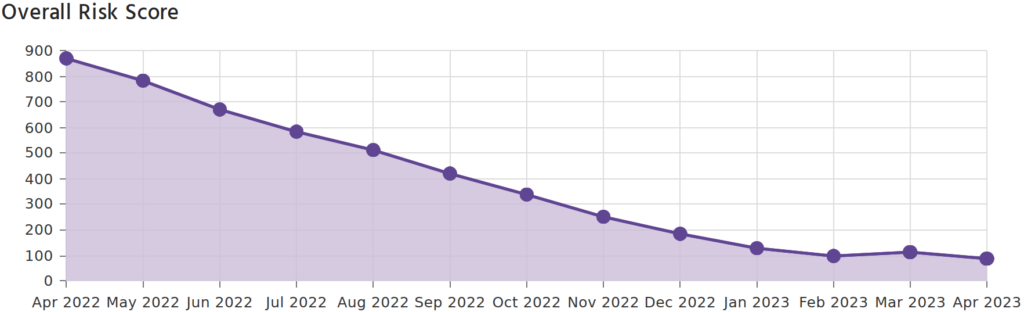
Implementing end-user training has been fantastic for both staff and IT security across the board. The training allows users to become more comfortable and confident with basic IT security, which is an essential in any modern workplace. The training is fun and interactive with short-form videos and quizzes to test the user’s knowledge. It targets user’s specific weak points and only takes a short time to complete.
Click below to watch an example of the training videos.
The training also reports back to us, to allow us to check-in on progress and risk factors for the company. As you can see it has amazing effects on the IT security risks within the business that are normally out of an IT services control.